Single Sign On (SSO) Implementation Process
About Single Sign-On (SSO)
The Connected World platform integrates SSO support for OKTA identity provider to allow users to login with their company credentials, thereby eliminating the need for users to maintain multiple sets of credentials. Keeping in view the selected protocol (OIDC), follow the related process steps to complete the information exchange to help Connectbase Support team to configure SSO for your organisation.
To configure SSO using OIDC protocol, follow the below process steps with Connectbase team.
SSO integration using OIDC protocol between your company and the Connected World platform requires an exchange of information between the two parties to establish the handshake and reroute to the company’s domain.
To get started, we provide you with the following information as your redirect endpoint url:
Please provide the following information to Connectbase team so that we can facilitate the handshake/reroute to connect to your IDP following the credential sharing process:
Domain Name
Client ID
Client secret
Issuer Endpoint
Authorization Endpoint
Token Endpoint
JWKS Endpoint
Domain rules (To be used in routing rules)
Following section provides more information on specific IDP providers that are supported by Connectbase today.
Depending on which IDP you are using, follow the below provided information for setting up SSO. For each IDP a link is provided for documentation as well.
Connectbase needs the following information for configuring Microsoft Entra Identity Provider:
Domain Name
Client ID
Client secret
Issuer Endpoint
Authorization Endpoint
Token Endpoint
JWKS Endpoint
For more information on configuring the Microsoft Entra Identity Provider process, follow the steps given in the below link:
https://learn.microsoft.com/en-us/entra/identity/saas-apps/openidoauth-tutorial
Connectbase needs the following information for configuring Okta Identity Provider:
Email Address Domain
Client ID
Client secret
If you are trying to configure SSO with OKTA identity provider, Connectbase would need URI from the customer OKTA Domain e.g connectbase.okta.com
For more detailed documentation on Okta configuration, follow the link below:
https://support.okta.com/help/s/article/create-an-oidc-web-app-in-dashboard?language=en_US
Note
Do not share your credentials/certificates using email or chat. Always follow the best practices for sharing credentials/certificates.
For Google IDP Connectbase requires the following information:
Customer Provided Information
Email Address / Domain
Client ID
Client secret
For more information on configuring the Google IDP, please follow the below link:
https://cloud.google.com/identity-platform/docs/sign-in-user-email
Follow the steps below to Google Identity Provider Configuration:
Click the below link:
https://console.cloud.google.com/projectselector2/apis/dashboard?supportedpurview=project&pli=1
If you already have a project, proceed by selecting an existing project.
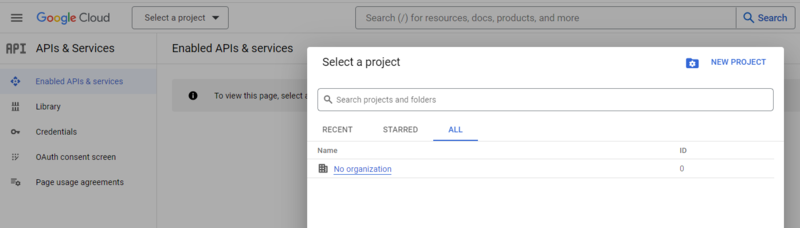
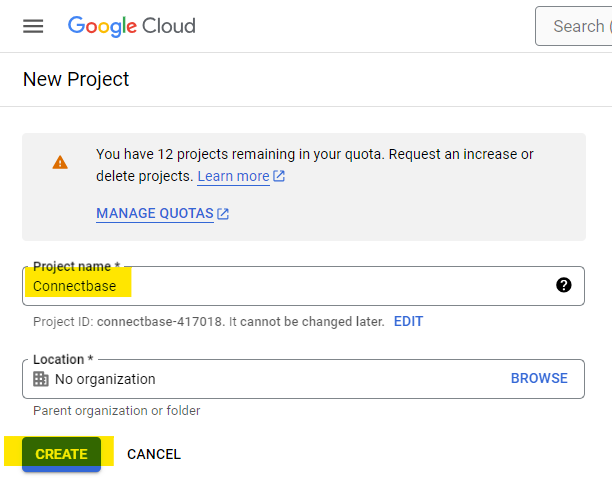
If not, create a new project as shown in the below example:
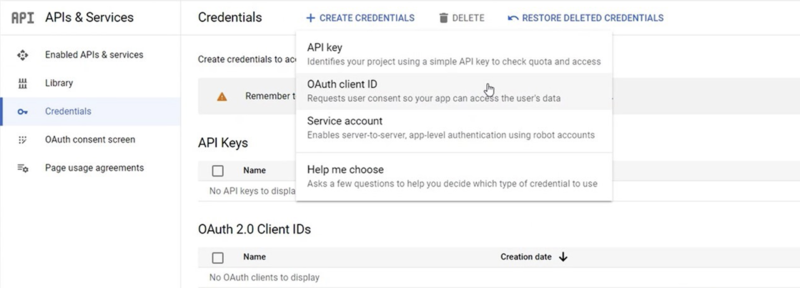
Go to the Credentials page
Click Create credentials > OAuth client ID.
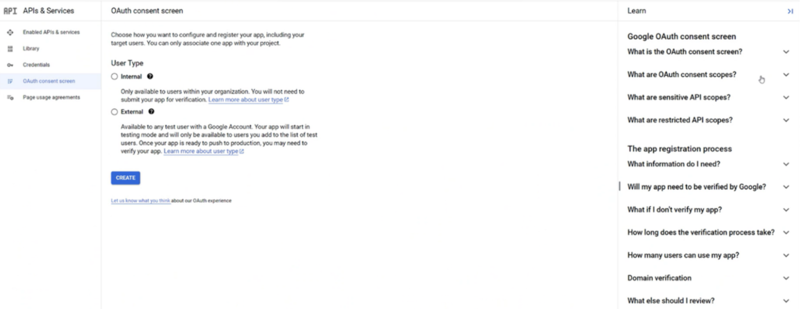
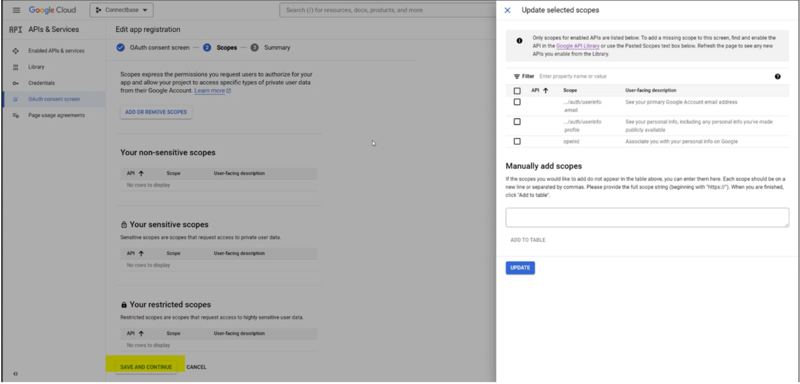
Click “CONFIGURE CONSENT SCREEN” button.

Select the Web application type = Internal
Name your OAuth 2.0 client and click Create
Add Contact Information and click “Save and Continue” .
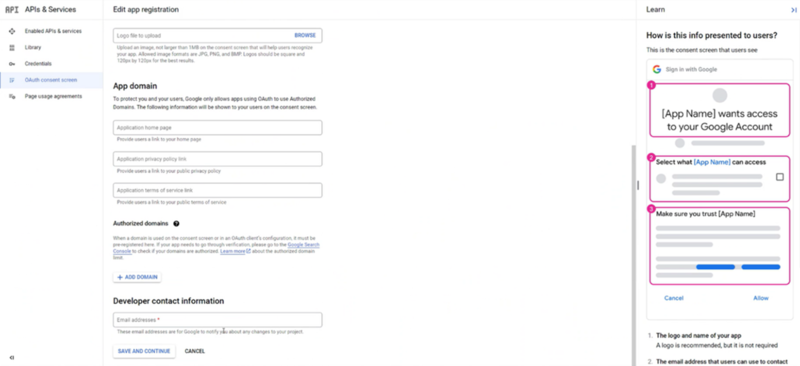
Add User Support Email for your app.
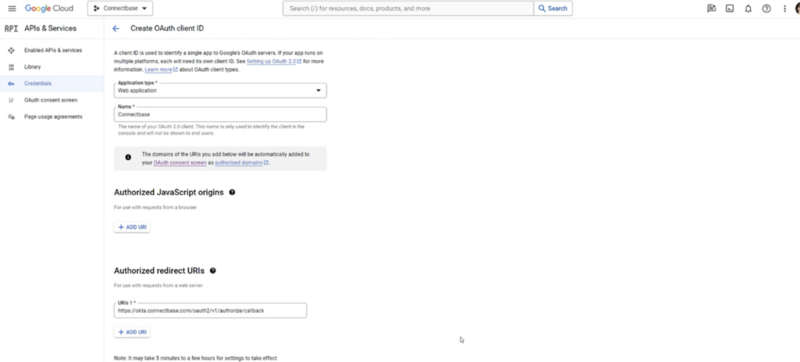
Confirm form with Application Type, Name you provided, Authorized redirect URI that Connectbase provided. Click Create:
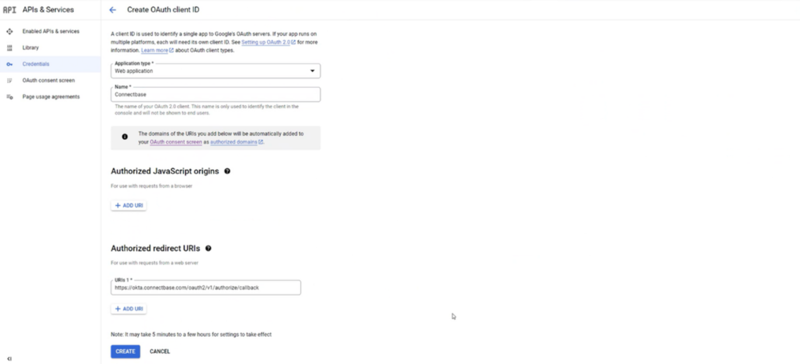
This complete app creation process.
If your organization uses an established secure method for sharing the above mentioned credentials with us, please follow that process to share the required credentials. This will enable the Connectbase team to configure your routing rules for SSO integration.
If you are not using an established secure method to share credentials as defined by your company, you can use the following method to share your credentials:
Attach the encrypted document to the ticket with a generated password that's shared either over the phone or based on a specific identifier like (Instance id+ a unique identifier).
Result: The Connectbase team completes the configuration using your shared credentials and updates the support ticket.
Once enabled within the Connected World platform, any employee logging in with your company’s domain is automatically redirected to the single sign-on page. Team management and role-based access control is handled by your identity provider rather than within the Connectbase platform.
SSO process steps
Company is enabled within their instance for SSO by an internal Connectbase Administrator
Once enabled, users log in using the SSO login button on The Connected World login page
The username entered is then redirected to the customer’s Identity Provider
User is signed into The Connected World